How to Change your Proxies?
About the proxy
What is a proxy?
A proxy refers to proxy software or proxy server, and can also be considered as a mode of network access.
Agents, as the name suggests, are used to do other things that things do not want or cannot do. For example, when you perform operations on a database, the agent can record the operation after you perform operations on the database. The function of a proxy server is to obtain network information on behalf of network users, and its basic behavior is to receive the request sent by the client and forward it to the target server.
How does proxy work?
Proxy service before the remote access, web data files, in the proxy at the bottom of a copy of the backup, if online set specified proxy, every time when in links to web pages, will check whether there are other people on the same site before, so you can back to the data directly, need not connected to the outside.
Figuratively speaking, it is the network information transfer station. Under normal circumstances, when we use a web browser to connect directly to another Internet site for network information, we contact the destination site server directly, and then the destination site server transmits the information back.
The proxy server is between the browser and the Web server to another server, with it, the browser to retrieve the Web page but not directly to the Web server to the proxy server requests, the signal will be sent to the proxy server, the proxy server and browser to retrieve the information they need to transfer to your browser.
The application of proxy
Proxy servers are like Bridges between two sides and are mostly used to connect to the INTERNET and INTRANET. But proxy servers are generally set access passwords or charge proxy fees.
What are the advantages of proxy?
1) Improve the speed of internal access
A proxy with a large bandwidth connects to the target host. Also, proxy servers usually have a large disk buffer (up to several gigabytes or more), like a large Cache, which has a lot of storage space. It constantly stores newly acquired data into its native memory.
When information with the outside world through, at the same time also save it to the buffer, if the browser on the requested data in its native storage already exists and it is the latest, when other users to access the same information, then it is not to fetch the data from the Web server, and directly by the buffer to retrieve information, to transfer the data on the memory to the user’s browser, In order to achieve the purpose of improving access speed.
2) Hide IP addresses, which can function as a firewall
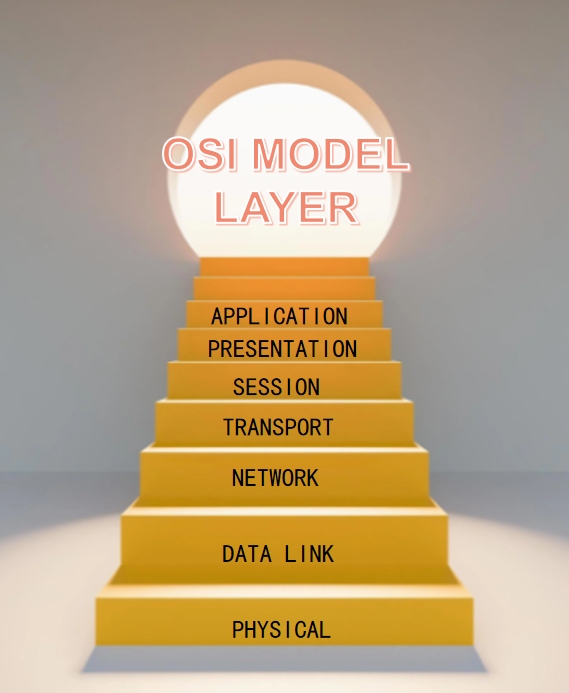
The proxy server is an important security function provided by the Internet link-level gateway, and its work is mainly in the dialogue layer of the open system interconnection model.
When all Intranet users access the external network through the proxy server, the mapping is only one IP address, so the external network cannot directly access the internal network. For a LAN using a proxy server, only the proxy server is visible to the outside world, and users of other Lans are invisible to the outside world. The proxy server acts as a barrier to the security of the LAN.
In addition, two unconnected intranets can also exchange information through a proxy server of a third party. All these can play the role of the firewall so that the security of Internet access has been improved.
3) Change your location
Using a proxy also allows you to access sites that you can’t directly access.
If you are studying or traveling abroad and find yourself blocked from accessing a local website, you are experiencing Internet access restrictions. Since the proxy provides you with a variety of IP options, you can choose the IP address of the city you want. You can select an IP address in your own country to access again or select some IP addresses allowed in your own country.
Also, since agents allow you to change locations, they can be used for social marketing. Because some Web services may behave differently in different locations, proxy IP can help consumers view social media ads or other activities from a user’s perspective.
4) Save IP overhead
The proxy server allows the use of a large number of “IP addresses”, saving online resources. Using a proxy server reduces the need for IP addresses.
For LAN access to the Internet, if you apply for an IP address for every user in the LAN, the cost is considerable. This problem is solved when you choose to use a proxy.
5) Block some access requests that affect the company’s internal traffic
For a LAN using a proxy server, only the proxy server is visible to the outside world, and users of other Lans are invisible to the outside world. The proxy server acts as a barrier to the security of the LAN.
6) Set limits on ports to prevent illegal attacks
The biggest advantage of proxy IP addresses is that IP addresses can be used to manage network resources and prevent some network resources from entering specific areas to protect the region of resources. High-quality proxy IP has great benefits for network security can make our computer from virus intrusion, especially for an enterprise, there is a lot of internal information, this proxy IP can greatly enhance security, in order to prevent the attack of hackers.
change your proxies
So, how do I set up or change the proxies? Keep reading!
1) Manually set the proxy
The address of the proxy server is similar to the address of any computer on the network, so if you already have an IP address and want to set it in your browser, you need to do the following:
- Open your browser and find the Settings option in the menu in the upper right corner
- Find network and Internet options and click in
- Select the proxy option, click Manual Settings, and enter the IP address and port you know in the address bar
- Save this information and exit.
2) Disable the proxy
Sometimes the proxy server prevents you from connecting to the network. If you want to change this, disable it.
If you can’t find the agent’s Settings TAB on your computer, you can find it in your browser. For example, go to the Settings TAB in the upper right corner of Chrome and find “Advanced” in the Settings list. Under advanced options, you will see “System” and then “Open your computer’s agent Settings”. Click on it and your computer will pop up the Agent Settings TAB. The proxy service is disabled from here.
3) Use ClonBrowser
Did it ever occur to you that you wouldn’t have to go to so much trouble to change your representation? Whether you’re looking for security or experience, ClonBrowser has everything you need.
First, ClonBrowser is an excellent virtual browser with strong proxy integration. Whether it’s 911, Luminati, Oxylabs, Vmess V2ray, ShadowSocks, etc., there are only proxy services you can’t think of, nothing you can’t use.
Second, ClonBrowser is an excellent privacy browser. If you want to change agents just to protect your privacy, ClonBrowser is for you! Because ClonBrowser isolates caches like cookies and uses mask fingerprints to keep the outside world from prying on you.
In addition, ClonBrowser allows you to create many configuration files and share them with your team to meet your multi-account needs. Start your free experience now!